Like traditional identity documents (IDs), wallets have always been our gateway to the crypto world. This article is about the Web3 cryptocurrency wallet and its differences from Web2 e-wallets like ApplePay or PayPal we used to know. In essence, the Web3 wallet also serves the purpose of storage and transactions like e-wallets in Web2. However, it improves the operating model, allowing users more freedom and security.
Web3 wallet landscape
The whole e-payments market is expected to reach 4.8 billion by 2025. Payment/wallet businesses have enjoyed revenue growth, especially since more and more applications are continually integrating with online payment.
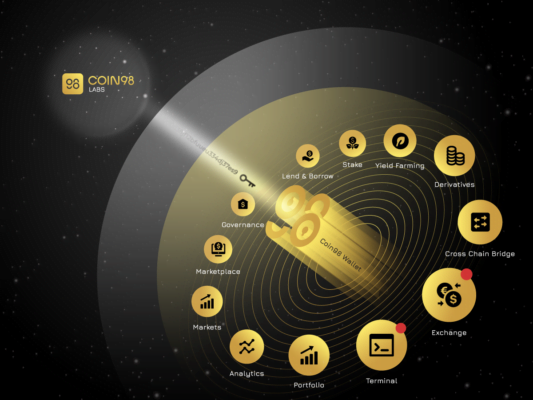
The number of investments poured into the Web3 wallet applications is approximately $3.3 billion. Recently, the leading web3 wallet company ConsenSys – Metamask raised $450M, bringing the company’s valuation to $7 billion. As more new ecosystems are launched, the number of wallet addresses increases significantly because no one wants to miss this “dreamland”. At the same time, the expansion of ecosystems leading to the primary development trend of Web3 wallet projects today is to deploy multi-chain wallets (Figure 1).
Figure 1. Web3 wallet landscape
Operating model
- The blockchain wallet can be interpreted as an interface for users to interact with the blockchain. Its primary function is to store assets or perform transactions.
- Blockchain wallets are divided into two types: custodial and non-custodial. We can also classify this according to the connection of the wallet: cold wallet (offline) and hot wallet (online).
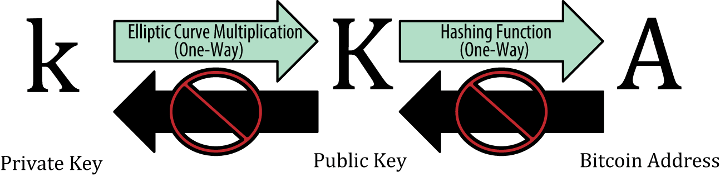
- Each wallet will include a public key & a private key: When a user creates a new “account”, an encryption algorithm will generate a private key; From the private key, generate a public key; From the public key, and generate a wallet address.
Note that this path only goes in one direction; there is no reverse (ie, no one can know the private key even if they know the wallet address).
- The private key works like a unique key to open your safe because every transaction on an account requires the signature of the private key.
Figure 2. How does a Bitcoin wallet work (Source: Blocktrade)
- The only difference between custodial and non-custodial wallets is who manages the private key. Like its name, non-custodial wallets require the user to keep and manage the private key themselves, while in custodial wallets, the private key will be stored by a third party.
Key storage
Commonly used methods to store secret keys:
- Store on hardware: this storage method is considered the safest, but they are also less convenient than the above storage methods.
- Local key storage: The key is stored on the device and can be accessed from software that points to a specific location in a database. Although convenient and fast, this method is not secure and vulnerable to attacks.
- Store with password (password-protected key): This method is similar to the above, but there will be an extra layer of security in the middle – only when the user enters the correct password then be able to access the private key. However, hackers can still steal passwords through spyware that tracks keystrokes or through brute force (a trial-error process on the computer to find the end result).
- Password-driven key: The password will be used as a control directly from the public-secret key pair. However, hackers can still attack this method by using random passwords to find these public-private key pairs (i.e. from the password “iloveyou” will find a corresponding key pair). Therefore, hackers can easily trace the private-public key pair of a user’s wallet address if he/she sets a weak password.
Model shifting
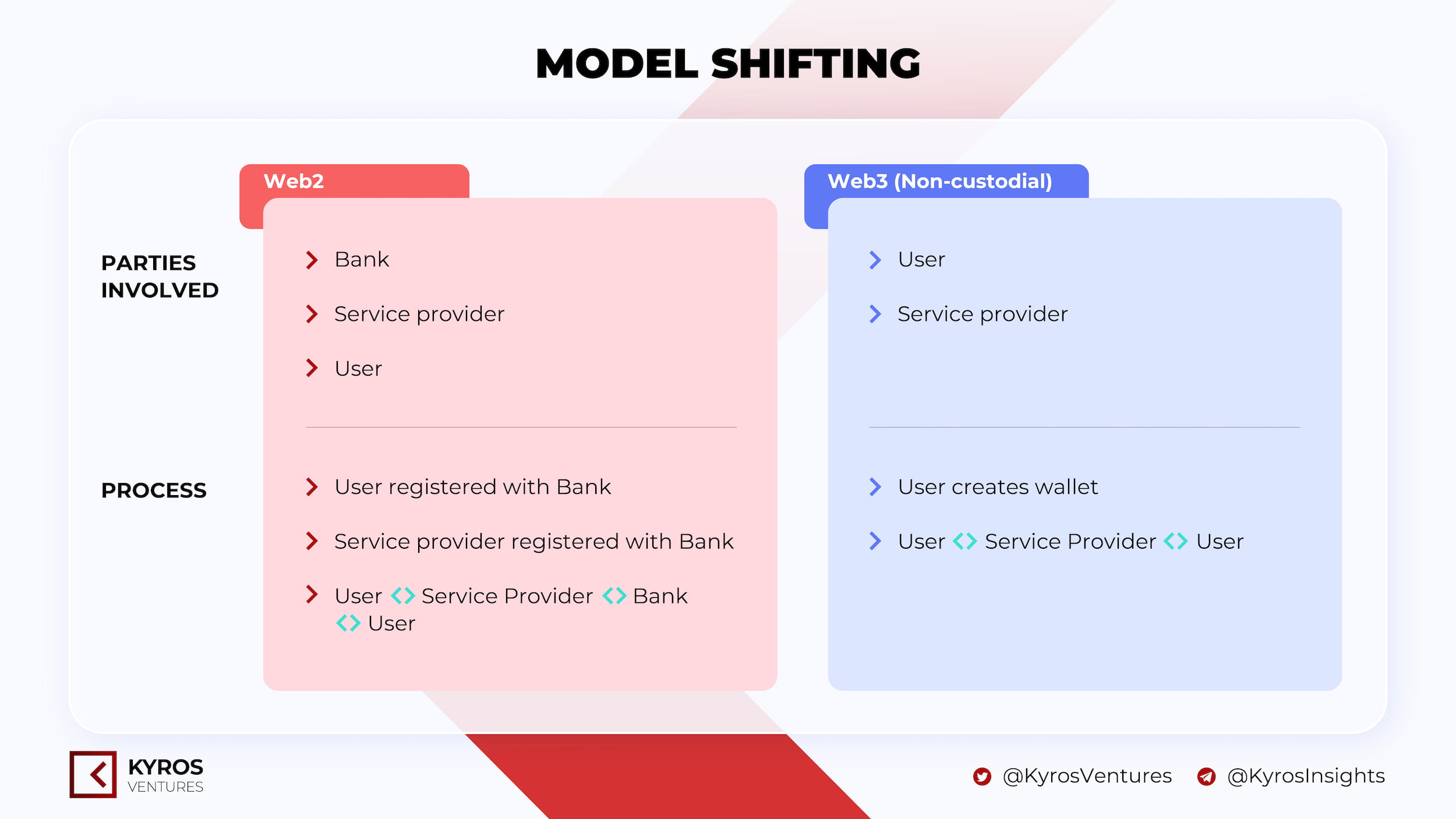
The model of e-wallets in Web2 involved three parties: User, Bank, and Service provider. Users need the participation of 3rd parties such as banks to store and confirm transactions and service providers to perform payments and connect between banks and senders/receivers.
A custody crypto wallet is a service provided by a centralized exchange like Binance and Coinbase. The service is to support you in keeping your wallet signature, meaning that they can keep and manage your private keys on your behalf. In other words, you won’t have full control of your funds nor the ability to sign transactions, which is similar to the e-wallet at Web2.
In contrast, with the non-custodial wallet model, users do not need to worry about intermediaries like banks because they have complete control over their wallets and assets. Because of cutting intermediaries, users do not need to go through the complicated authentication process steps or share personal information (Figure 3).
Figure 3. E-wallet model shifting
Key functions to retain user
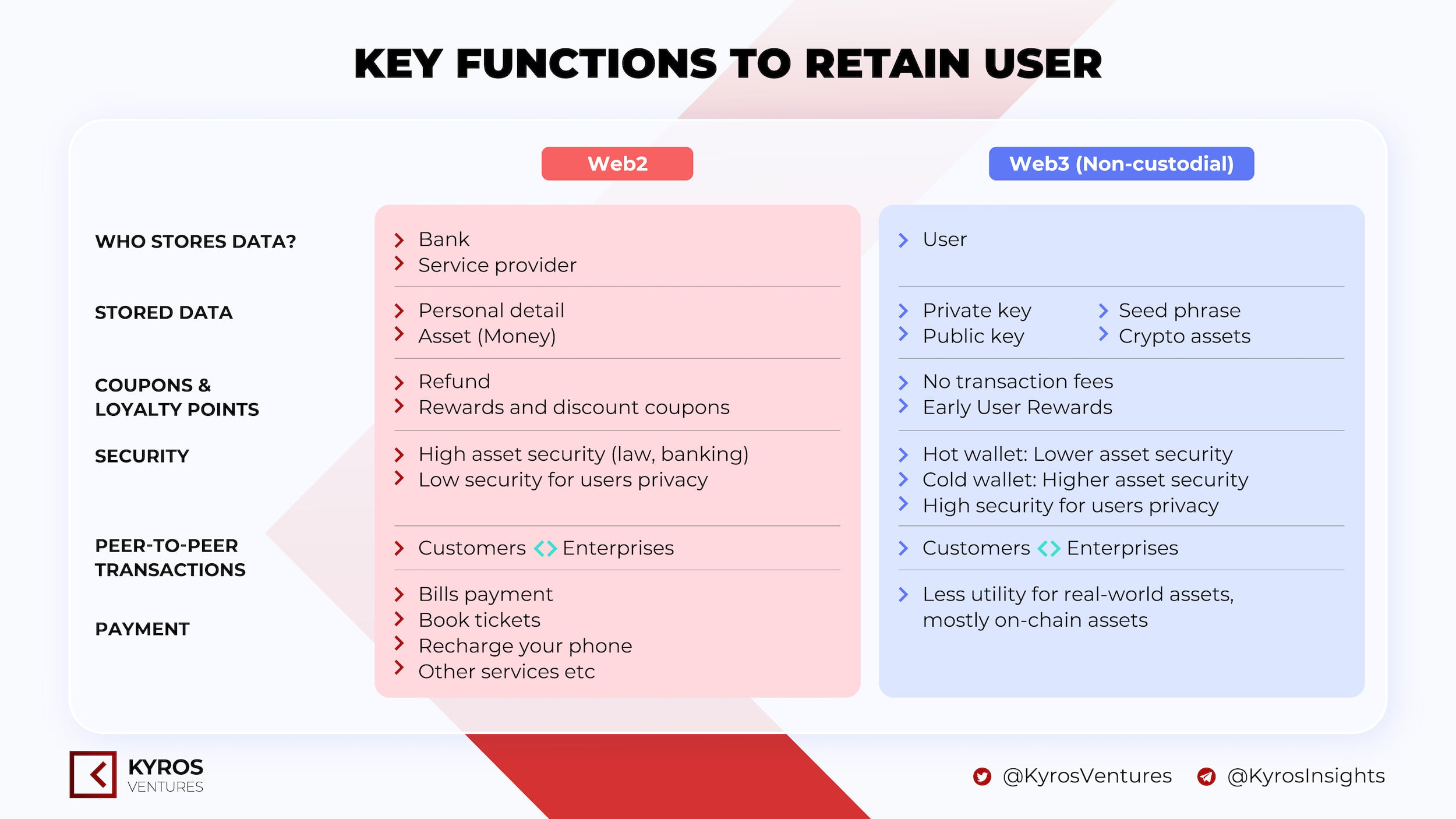
Figure 4: Key functions to retain user
The Web3 custodial wallet model has similar characteristics to the Web2 e-wallet, so it is suitable for less experienced users who need 3rd party support. Custody wallets such as Binance Custody are compliant and provide standard coverage for Binance accounts. Therefore, providing more legal security for the user in exchange for the user’s personal data (KYC).
On the other hand, privacy protection is one of the most prominent features of Web3 non-custodial wallets (Figure 4). User personal data is safe and secure when it no longer needs to be provided to any 3rd party. Thus, it is possible to prevent the relevant leaking information actors.
In terms of security, hardware wallets have the highest safety, suitable for users for long-term investment and storage. Hardware wallets are not directly connected to the internet, thus ensuring a high level of security for large sums. Hot wallets are less secure and more vulnerable to attacks because they are stored and frequently interact over the internet. Recently, we saw a leak of users’ private keys from the Slope wallet platform, with a total loss of up to 6 million USD for users.
To solve the aforementioned security issues, Vitalik has come up with a solution called social recovery wallet. They combine the ease-of-use of single-signature wallet with the better security property of multi-signature wallet by adding a group of guardians: in case everything runs smoothly, users still use the social recovery wallet as the normal single-signature wallet, but in the case of being hacked, the wallet’s owner can send a request to the guardians group to change the current signing key of the hacked wallet to a new one of the owner (but they must wait 1-3 days to execute this). Nevertheless, the current infrastructure of Ethereum does not allow for direct implementation of social recovery wallet but a third-party relayer who will be responsible for re-submitting signed messages as transactions to the blockchain, adding up the transaction fees as well as the centralization of the protocols.
In terms of payment application coverage, Web2 wallets can pay for almost anything, especially in countries with mature financial infrastructure. Whereas Web3 has less utility for real-world assets, payments are primarily made to on-chain purchases. However, there have been more positive signs as more brands and products accept crypto payments, opening the door to growth for Web3 wallets.
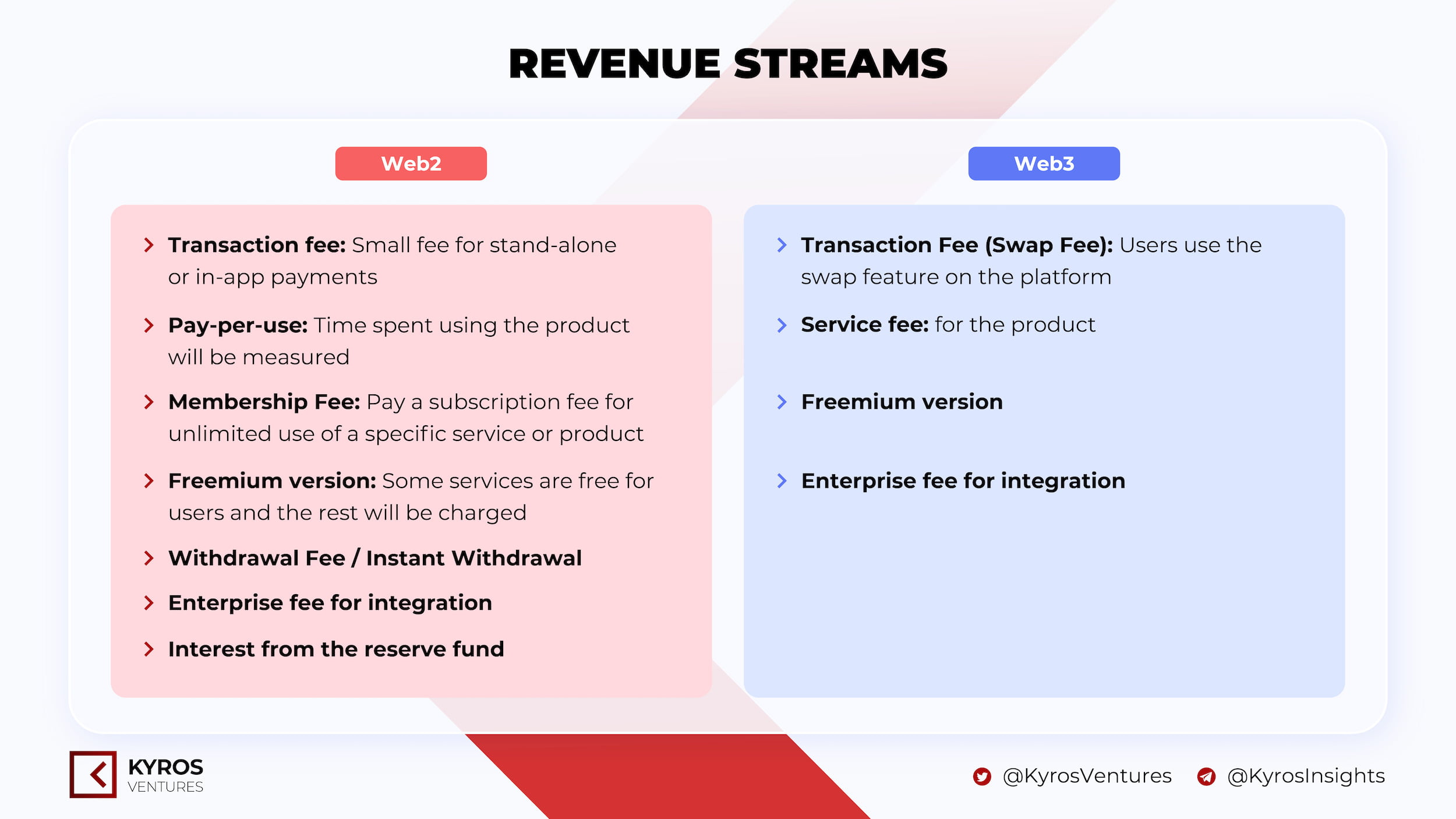
Revenue streams
Figure 5: Revenue streams of Web3 wallet
Some examples for web3 wallet revenue models:
- Transaction fee:
- Metamasks charges transaction fee from 0.3% – 0.875%.
- Phantom charges a 0.85% fee for all transactions.
- Enterprise fees for integration: MetaMask offers MetaMask Institutions (MMI), an “institutional extension” of the MetaMask wallet specifically designed for funds speculators, crypto funds, financial institutions, market makers, etc.
- Freemium version: Trust Wallet is free for users. All fees are paid to miners or validators. In addition, Trust Wallet also launched the $TWT token to control its own economy.
In general, Web3 wallets are heading towards building many different features aimed at acquiring and retaining users. Meanwhile, the main and most sustainable source of income is still transaction fees. Thus, we can view the Web3 wallet model as a variant of DEX that focuses more on payment and transaction utilities than DEX.
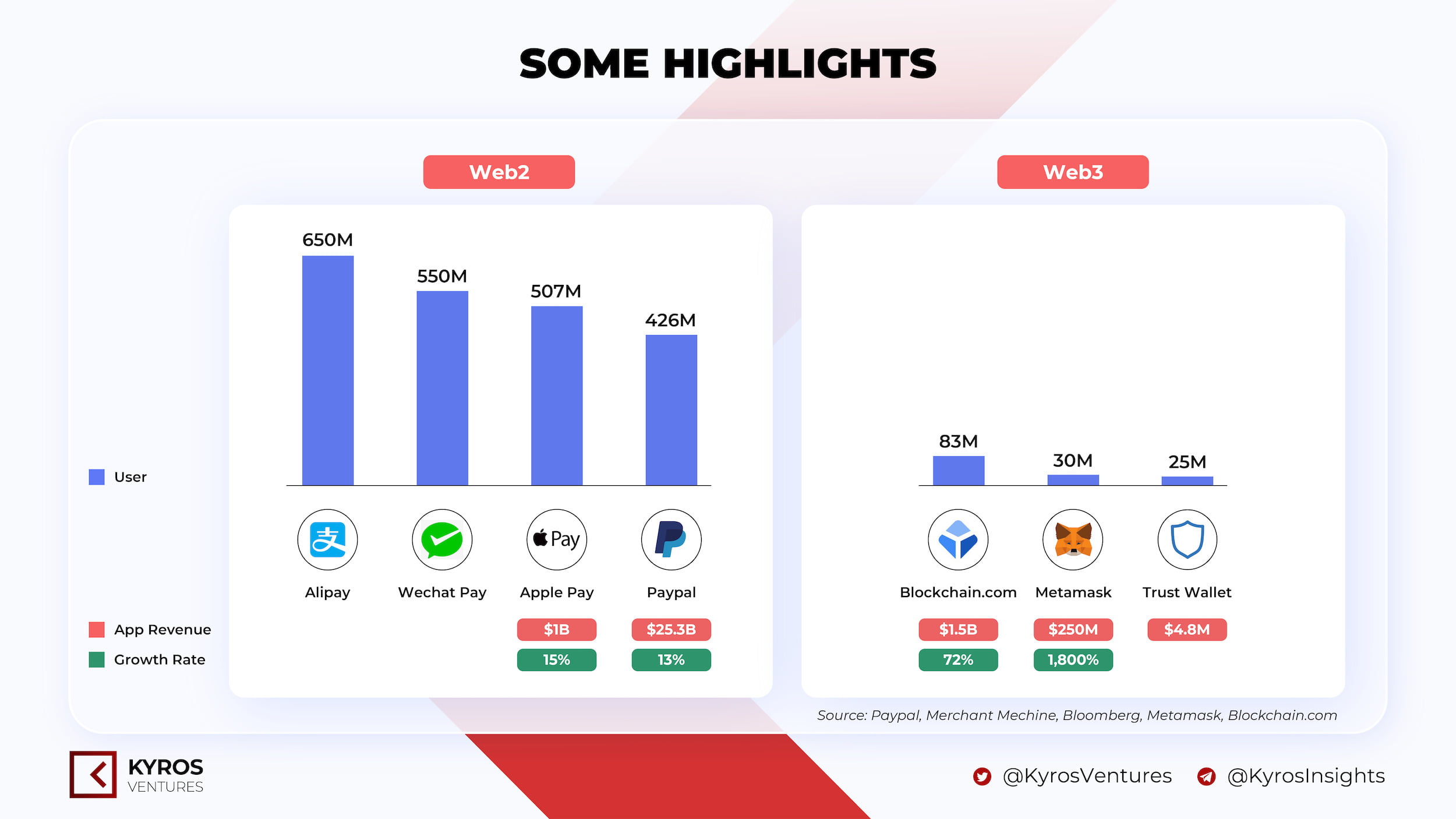
Some highlights
- In Web2, the number of e-wallets is up to 2.8 billion wallets. Meanwhile, Web3 only reached about 300+ million wallet addresses. Obviously, Web3 has much room to expand further to reach the number of users who have used e-wallets in the past.
- In addition, Web3 wallet applications witnessed impressive growth in 2021: Metamask is up 1800% and blockchain.com is up 72%. A large part of the growth in the number of Web3 wallet addresses is due to the GameFi/NFT boom in 2021.
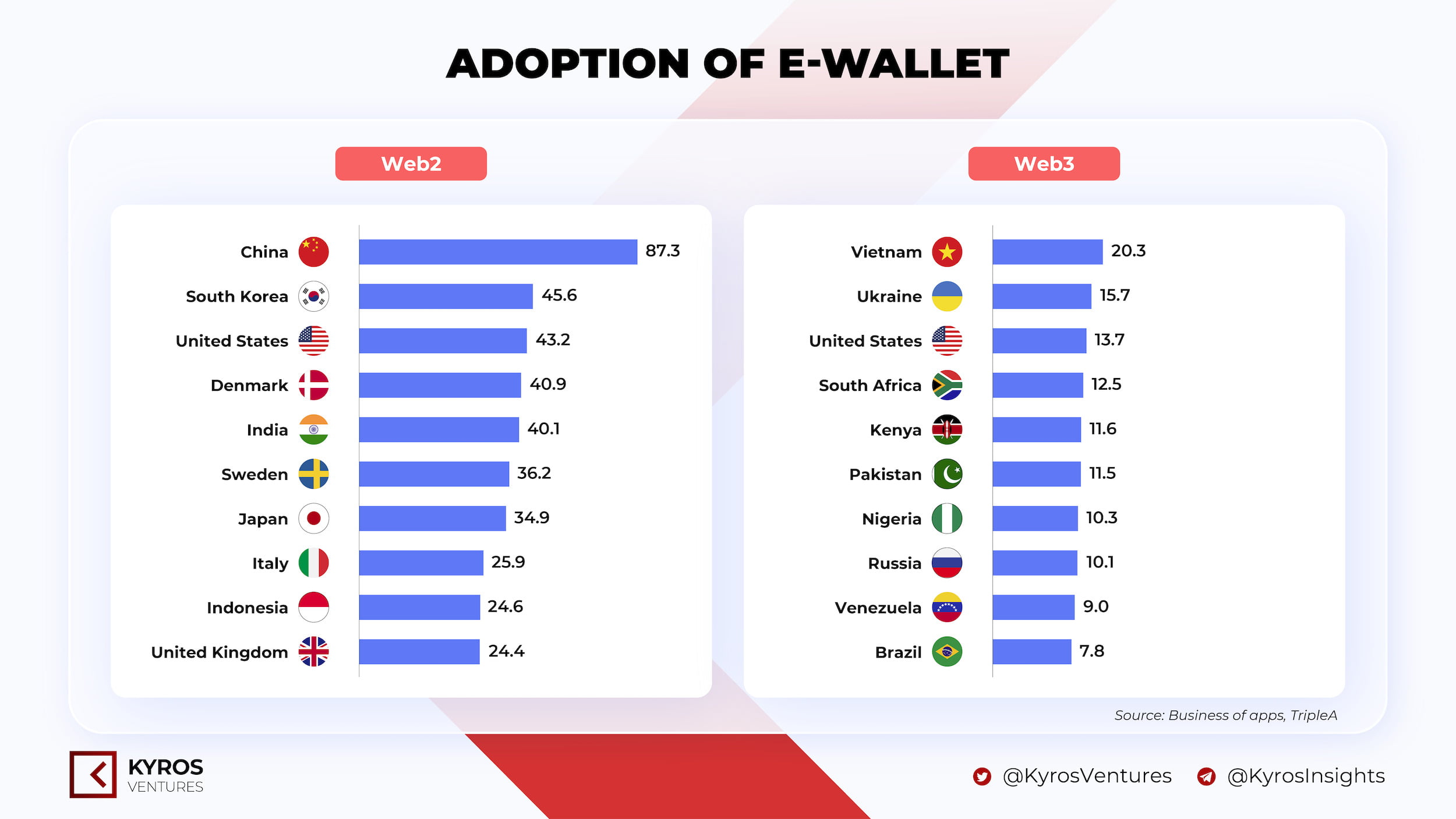
Adoption of e-wallet
- Southeast Asia and the Middle East will continue leading the growth of Web3 wallets due to their limitations with banking and credit cards. In other words, because of lacking financial instruments, the chance for web3 wallets to develop in these regions is higher than in countries with fully established financial systems. One example is the rise of the Axie Infinity game, which has brought a new inflow of users into the cryptocurrency market. Most participants are in developing countries, and Axie opens up new financial opportunities for users in these regions.
- Slow growth in Western Europe, North America and China, as these are not crypto-friendly countries. These regions have a complete financial infrastructure, providing a variety of online financial services to the people. In particular, crypto creates problems with illegal money transfers and destabilizes the financial systems of these countries.
What’s under development
- Integration: MetaMask launched Snaps earlier this year, a system that allows developers to extend and customize MetaMask wallet features in a different coding environment. Users are free to experiment with these new features, and the MetaMask team will consider integrating the most popular feature into their final product.
- Multi-chain: This is an inevitable trend that almost all wallets aim for. The shift to multi-chain helps users conveniently transact between different chains on a single wallet interface. It also helps them better manage their assets by only having to store one private key/seed phrase instead of many complex private keys for different chains.
- Simplify UX: Many new features have been launched to help users directly buy/sell/list coins or NFTs in the wallet. It even cooperates with CEX exchanges to shorten the time of transferring tokens between non-custodial wallets and CEX exchanges.
- Native swap
Roses are red🌹
Violets are blue
But first, let’s check
What Native Swap brings to you?No more manually checking on multiple AMMs to find the best prices. Just select Blockchain & proceed with your transaction right away🚀
Get your #Coin98 updated 👉https://t.co/kkvXVJEcoQ pic.twitter.com/97bJNdO7Os
— Coin98 Super App (Formerly Coin98 Wallet) (@coin98_wallet) August 4, 2022
- Direct listing
Listing NFTs on @MagicEden from Phantom is available to everyone on all devices! Did you know that you can also use your wallet to edit prices and remove listings?
It’s super convenient from our mobile apps when you (or floor prices) are on the move!! 🧹🧹 pic.twitter.com/OeLIrKYlIG
— Phantom (@phantom) July 28, 2022
- Social recovery wallet: social wallet brings more convenience for users to get their assets back if they lose or get hacked into their wallets. The confusing numbers of private key or mnemonic passphrases will no longer be a big obstacle for users.
- New revenue models: The revenue generation models of Web3 wallets were “imported” from Web2, but there has not been much improvement in adding revenue. The revenue from transaction fees still contributes to the bottom line in bringing profit for both the e-wallets in Web2 and Web3. In the future, Web3 wallets will need to introduce new features, not swaps, stakes, or yield farms but also products that provide data to help users with their better investment strategies. Additional services such as insurance, in-app shopping, consulting, etc., in Web2 can be extended to Web3 wallets. Although these services cannot replace the primary source of revenue from transaction fees, it will diversify products to attract and retain users.